If you use Azure runbooks and utilise scripts which connect to Office 365 services you will run into issues if the account you use to authenticate has MFA enabled on it.
One option is to bypass MFA on the account for any connections coming from a specific Azure datacenter. This doesn’t open up the account to the internet but please understand that anyone trying to access your account from the same datacenter will also be able to bypass MFA. Also for this to work you will require an Azure AD Premium P1 or P2 license.
With that understood lets go..
Log into the azure portal here
Click on Azure Active Directory.
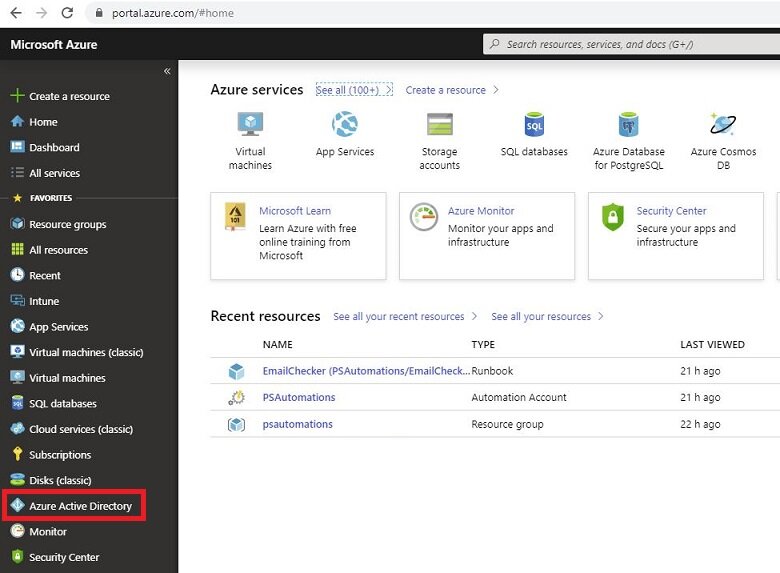
Click Security.

Click Conditional Access

Click Named Locations.

Click Configure MFA Trusted IP’s.

Tick the box ‘Skip multi-factor authentication for requested from federated users on my internet’ and enter the IP’s assigned to the datacenter of your tenant. (See how to get these IP’s below).

Microsoft maintains a list of all Datacenters and their associated IP ranges here.
https://www.microsoft.com/en-us/download/details.aspx?id=56519
Download the json file and open it up in notepad. Locate the AzureCloud entry associated with your Datacenter location. My own lab tenant is located in UK South.
Once you locate the section for your location you can copy out all of the IP ranges and enter then as trusted IP’s to bypass MFA.

Conclusion
All of your Global Administrator accounts must have MFA enabled but this does mean that unless you are using the latest authentication frameworks in your scripts they wont run. Currently Azure Runbooks can’t be set to run from a dedicated IP address which would improve security. For now if you wish to run scripts which require authentication to Office / Microsoft 365 services you must use the above method.

Leave a Reply