When using Teams as a collaboration platform, you or your clients might engage with external businesses. The conventional method for adding outside users is to invite them as guests and grant them permissions to your Teams/Channels. However, in situations involving long-term projects with many departments or users from a collaborating organization, or when partnering closely with a sister company that operates under a separate tenancy, the Azure B2B Direct Connect Trust relationship becomes relevant. Currently, this solution has some limitations, but I expect its capabilities will grow over time. The main advantage of Azure AD B2B Direct Connect is the ease of adding users from a trusted tenant to a shared Teams Channel, allowing visibility within their Teams without switching organizations. However, it’s important to note that B2B Direct Connect may not suit everyone, particularly if the collaborating party does not utilize Azure AD for identity management. Microsoft outlines the distinctions between B2B Direct Connect and B2B collaboration in Teams here:
- With B2B Direct Connect, you add an external user to a shared channel within a team. They can access resources within that shared channel but do not have permissions to the entire team or other resources beyond the shared channel. For instance, they won’t be able to access the Azure AD admin portal, but they can use the My Apps portal. Users connected via B2B Direct Connect won’t have a presence in your Azure AD organization and will be managed through the Teams client by the shared channel owner.
- Using B2B collaboration, you invite the guest user to a team. The guest user accesses the resource tenant via the email address used for their invitation, and their access is governed by the permissions set for guest users in the resource tenant. Guest users are unable to see or take part in any shared channels within the team.
Let’s briefly explore setting up Azure AD Direct Connect with two test tenants, adding users from the trusted tenant to a shared Teams channel, and the user experience for the collaborating user.
Establishing the B2B Direct Connect relationship is straightforward. You’ll need the other tenant ID or domain name (both organizations must complete these steps). Navigate to Azure AD > External Identities > Cross-Tenant Access Settings. Here, click Add Organization and enter the tenant ID or domain name. As mentioned earlier, both collaborating Azure AD tenants must complete this step. In this scenario, my tenant (ganlab) and a test tenant (1rry0) are collaborating.
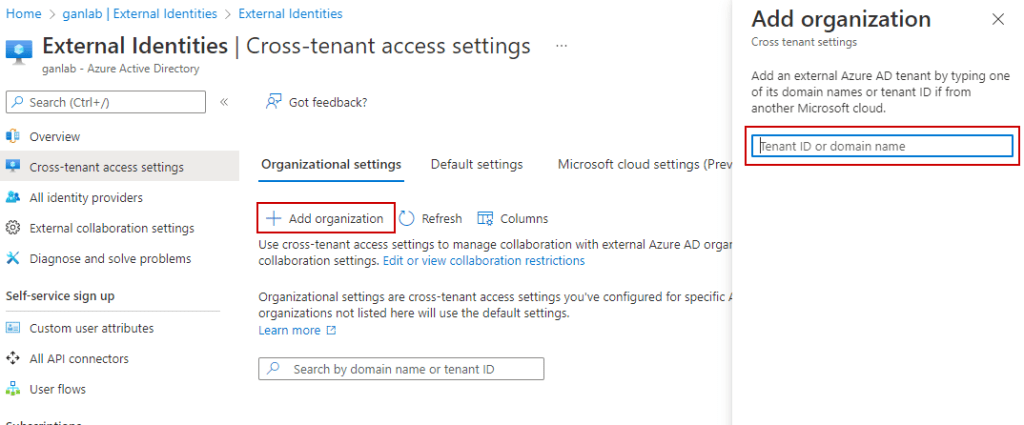
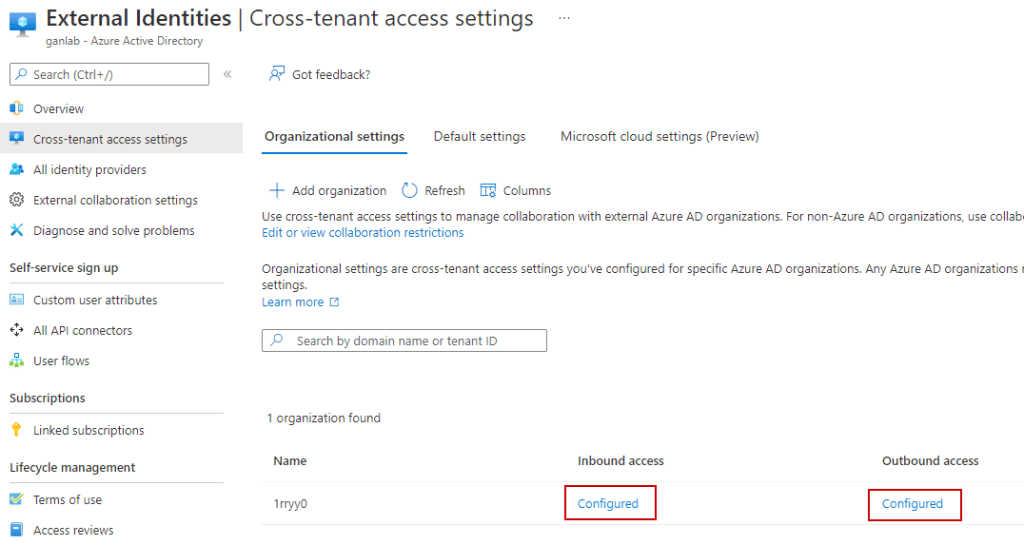
After adding the organization, it’s time to configure permissions. You may restrict this to specific groups or users from the collaborating organization if desired (note that if you do, you’ll need the object IDs of the users or groups in the other tenant). In this case, I’m permitting access to all users & apps. Click on the inbound access and outbound access links (keep in mind that the other tenant must also complete these steps for your organization):
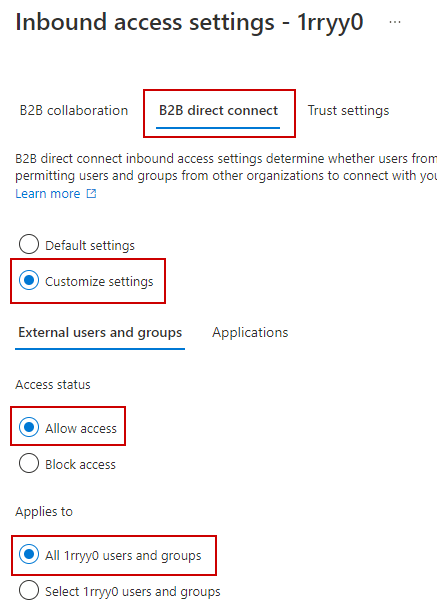
B2B Direct Connect defaults to block settings. Change to Customized settings and edit the access:
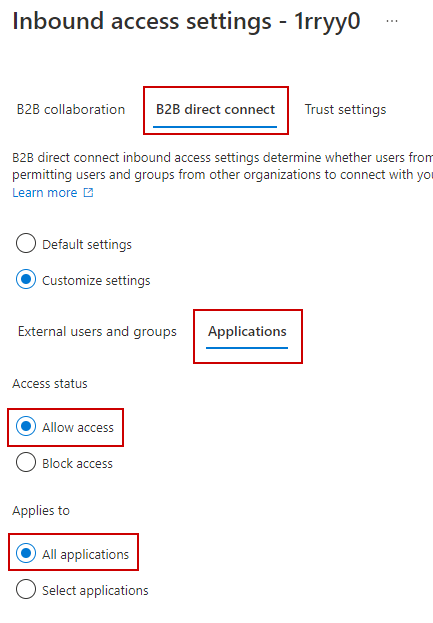
Similarly, do this for the application access:
Finally, if your tenant employs conditional access policies for MFA and/or mandates a compliant device for accessing company resources, trust must be established for MFA and compliant devices from the other tenant:
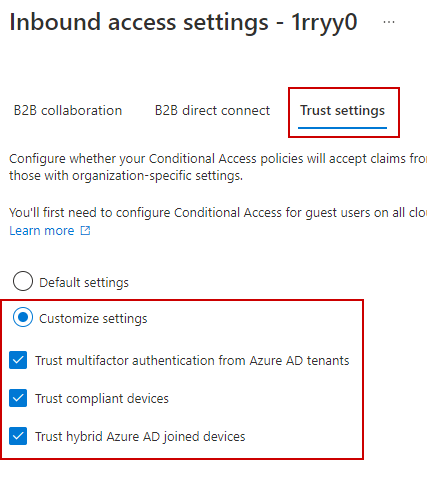
Make sure to finalize the outbound settings as well:
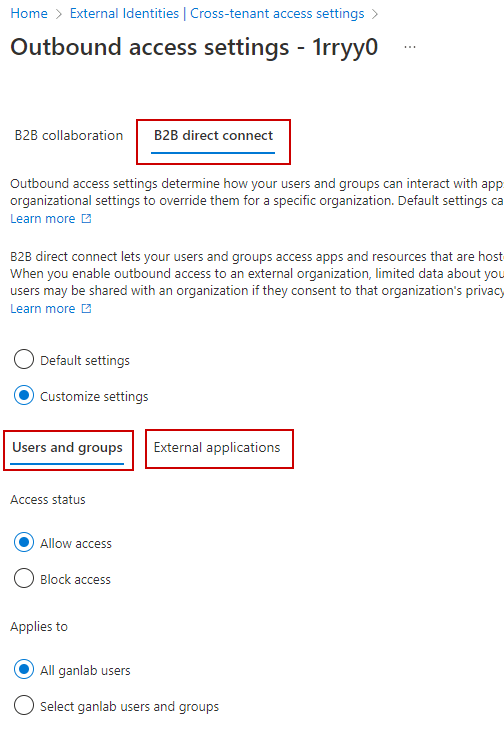
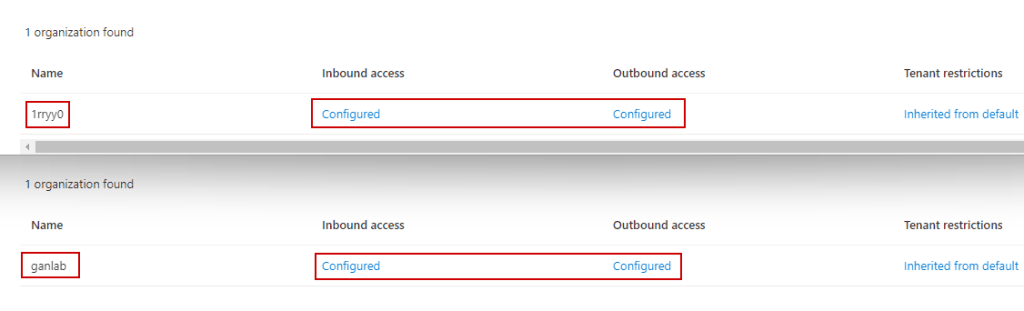
With the inbound and outbound settings configured in both tenants, you can now attempt to add users to a shared Teams channel. Below is a screenshot from both tenants displaying the configured B2B Direct Connect access settings:
Now, let’s create a shared channel for collaboration with the trusted organization, which I am doing in my ganlab tenant. Sign in to Teams admin center, locate the Team you wish to add a shared channel to, and proceed to add a channel.
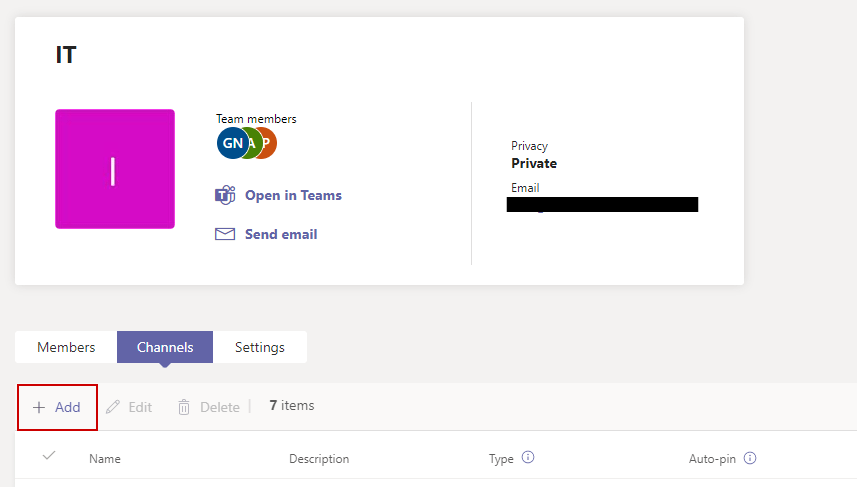
Ensure you select Shared as the channel type and assign at least one owner. Teams admins or channel owners have the authority to add users to a shared channel.
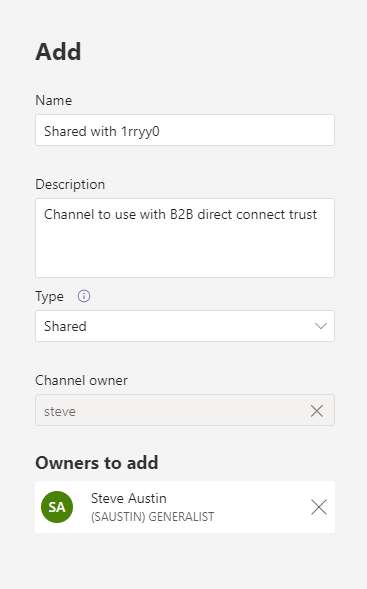
Next, let’s add a user from the other organization established through B2B Direct Connect. If users don’t appear immediately, you may need to wait, as in my case it took about 30 minutes after establishing the B2B Direct Connect relationship before I was able to add users from the other tenant:
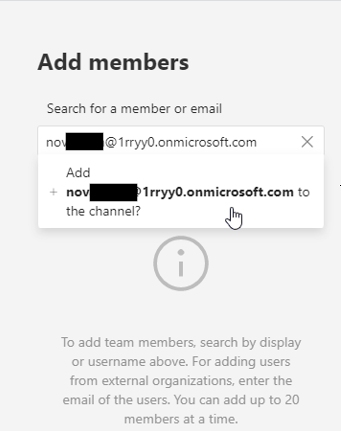
Now, let’s manage the channel in Teams and observe the external identity from the other organization:
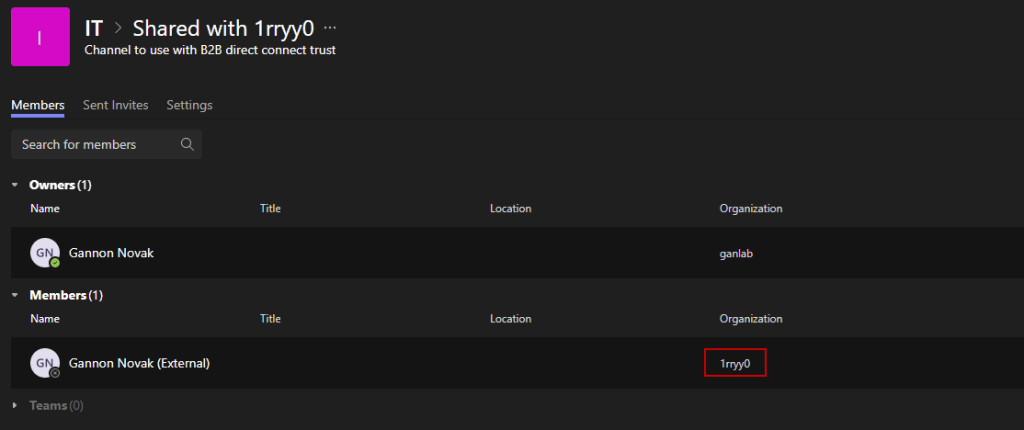
Signing in with the account from the 1rryy0 organization, I can view the shared channel from ganlab within my Teams without needing to switch organizations. Only the shared channel is visible. It’s hoped that Microsoft will eventually enable full Team access:
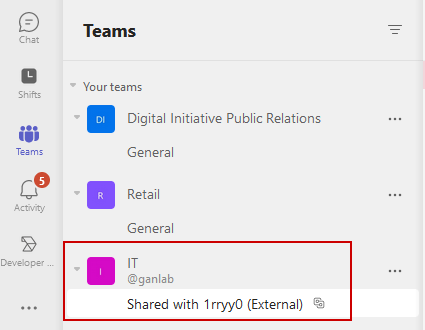
The chat box indicates that the channel is shared with other organizations:
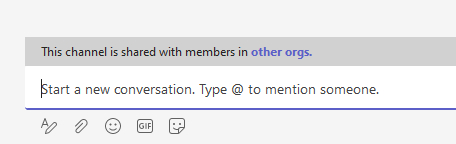
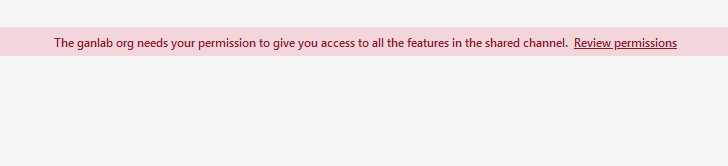
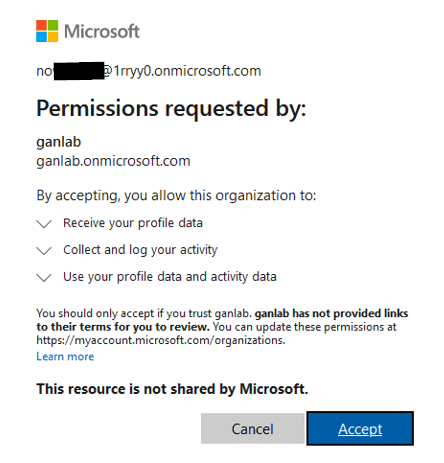
Collaborating users will need to review and accept the permissions the first time they access the channel:
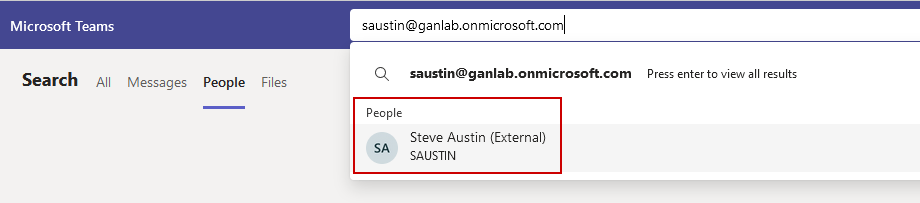
Additionally, you can effortlessly chat with users from the other organization by searching for them. The upper screenshot shows a user from the trusted tenant (1rryy0) chatting with someone from my tenant (ganlab), while the lower screenshot depicts me searching for a user in a non-trusted tenant.
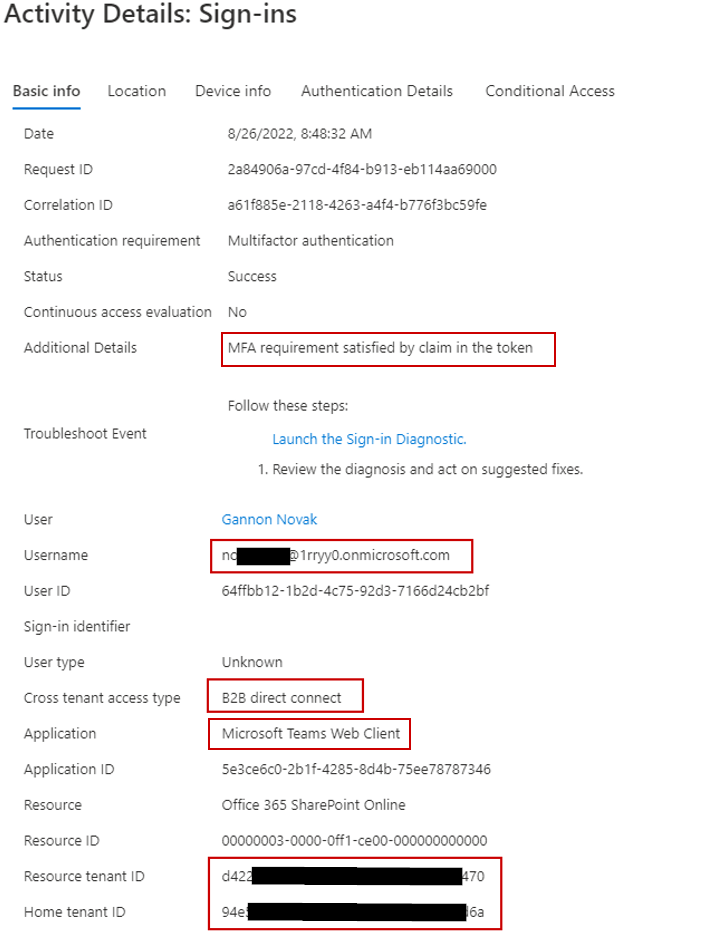
Lastly, let’s examine the sign-in logs for my tenant. It’s essential to note that B2B Direct Connect does not create user identities for the collaborating users in your Azure AD; it simply establishes trust with the other tenant. Observing the sign-in log for the 1rryy0 user in my tenant (ganlab), we notice some interesting information. The username displays the full name of the visiting user, indicates that MFA has been satisfied by the other tenant, confirms that the cross-tenant access type is B2B Direct Connect, and provides the resource and tenant IDs:
Official Microsoft resources:


Leave a Reply